🧙♂️ What is the objective of a security function?
The Fellowship - Twelfth edition
Welcome to the twelfth edition of The Fellowship Newsletter.
Last week, I wrote about the Top 5 things to look for in a Course Hosting Platform. I wrote it to help those thinking about launching your own course. It took me a lot of research to determine what I needed and which platform to use. I hope it helps you save a few hours.
This week, I want to cover a subject I touched on in the How to Choose a standard edition of The Fellowship. Like last week, I’m still on holiday from work, so it won’t be narrated. I’ll get back to that next week. The subject for this week is:
What is the objective of a security function?
Before answering the question, we need to know what we mean by “Security.” It’s from the Latin word. “Securitas”. It means to have “freedom from care”. If we dissect that a little more, It’s a feeling of “Freedom from Harm”. It’s a feeling of comfort and safety where you are and in your activity.
So, we know that being secure means feeling comfortable and safe. Why, then, do people feel insecure? There are a few reasons. The first is Natural disasters. Things that happen in our surrounding area could cause us harm. Things like tornadoes, tsunamis, and earthquakes (I’m including man-made object failures in this category (e.g., Aircraft failures, Building collapse, and Electrical fires)). Things that occur where we have zero control over what happens to us.
Then we have Animals. They are not dangerous all the time. Animals are potentially dangerous. Most people who animals harm put themselves in danger in the first place. But they can still make us feel insecure! If this lion is walking towards me and you when out for a walk together, we will both feel insecure. If I start running… you’d better keep up because it’s the slow one that gets eaten.
We can control none of those things. It’s not in our remit as a security function to concern ourselves with it. What we can do is to focus on people. Other people's behaviour can cause feelings of insecurity, either in our staff or our customers. People can be unpredictable, manipulative, aggressive, and violent.
Our staff want to avoid coming to work and fear being harmed. Likewise, our customers do not want to be impacted by the unwanted behaviour of someone who has access to our networks and systems, potentially causing harm to their staff or customers.
That fear of harm does not always come from external forces. Accidental actions or incompetence can also cause damage. A system administrator wiping the backups, or someone in HR sending staff compensation rates to the wrong distribution list. Then there is also the possibility of Insider Threat. Someone internal to the organisation acting against it or working in their own self-interest to defraud the organisation of money or future revenue.
Given that we now know that being secure is all about feelings, what is the purpose of the security function? Why are we here?
The primary objective of the security function
To advise the organisation on safeguarding operating conditions to prevent behaviour impacting its ability to create protected value.
The secondary objective of the security function
To identify and respond to occurrences of unwanted behaviour that were able to avoid the safeguards and implement countermeasures to reduce the impact of possible harm.
There is a beautiful quote that I use when I talk about security risk. It’s by the author J. A. Shedd, who lived between 1859 and 1929. He stated:
“A ship in harbour is safe, but that’s not what ships are built for.”
This sums up quite nicely what we do in security. We advise businesses on how to build their ships to deliver their goods safely to their customers. Essentially, we advise them on how to build and manage their operating conditions so that they can do business in places where unwanted behaviour causes them (or their customers) to feel insecure. In our case, that is mostly business operating in the online environment.
Safeguarding Operating Conditions
We must safeguard our operating conditions, but how do we do it? We need to introduce controls to prevent it. Safeguards are chosen to reduce the frequency of a behaviour or event that could cause harm. These controls act as blockers to prevent access to the environment you wish to protect. Countermeasures are chosen to reduce the impact or level of damage the behaviour could cause.
Control Sub-types
Preventative controls stop something from happening.
This would include VPNs, Network and Application Firewalls, and Security Groups in the cloud.
Detection controls provide awareness that an event of concern is happening.
This would include SIEM tools like Splunk and SentinelOne.
A corrective control stops an event from progressing any further.
This might include an endpoint detection and response tool that stops known malicious files from executing. Think CrowdStrike and Windows Defender.
A displacement control moves the event to where the potential for harm is reduced.
This could be a Honeypot or a Sandbox with no production data.
A minimisation control reduces the impact of the event.
This could include methods of preventing someone from downloading the entire customer database in one request. Instead, breaking the download into very small chunks and requiring the approval of 2 other people.
Recovery controls reduce the effect of the behaviour.
This would include Data Backups, Incident Response Policy, and Business Continuity Procedures.
Awareness and Capability controls are people-based controls.
This usually involves training and testing.
Accidental Data Loss
Security is a people problem. Generally, people want to be good. They want to go to work, do a good job, get paid, and go home. They don’t want to do something that might jeopardise that. But work is complicated. There are lots of things to think about. Some pressures put on our staff can make them do things accidentally that cause harm.
Between 70 & 90% of instances of data loss are caused by someone internal to the organisation.
That is where our Security Policies and Procedures come in. These are our Authority documents. These are how we influence most of our staff. We set rules that we want them to do. These are Administrative and Managerial controls. Without this guidance, we, the staff, are the vulnerability. They are the basis of how we implement our safeguards and countermeasures. They are the Root of all Control. Let me explain:
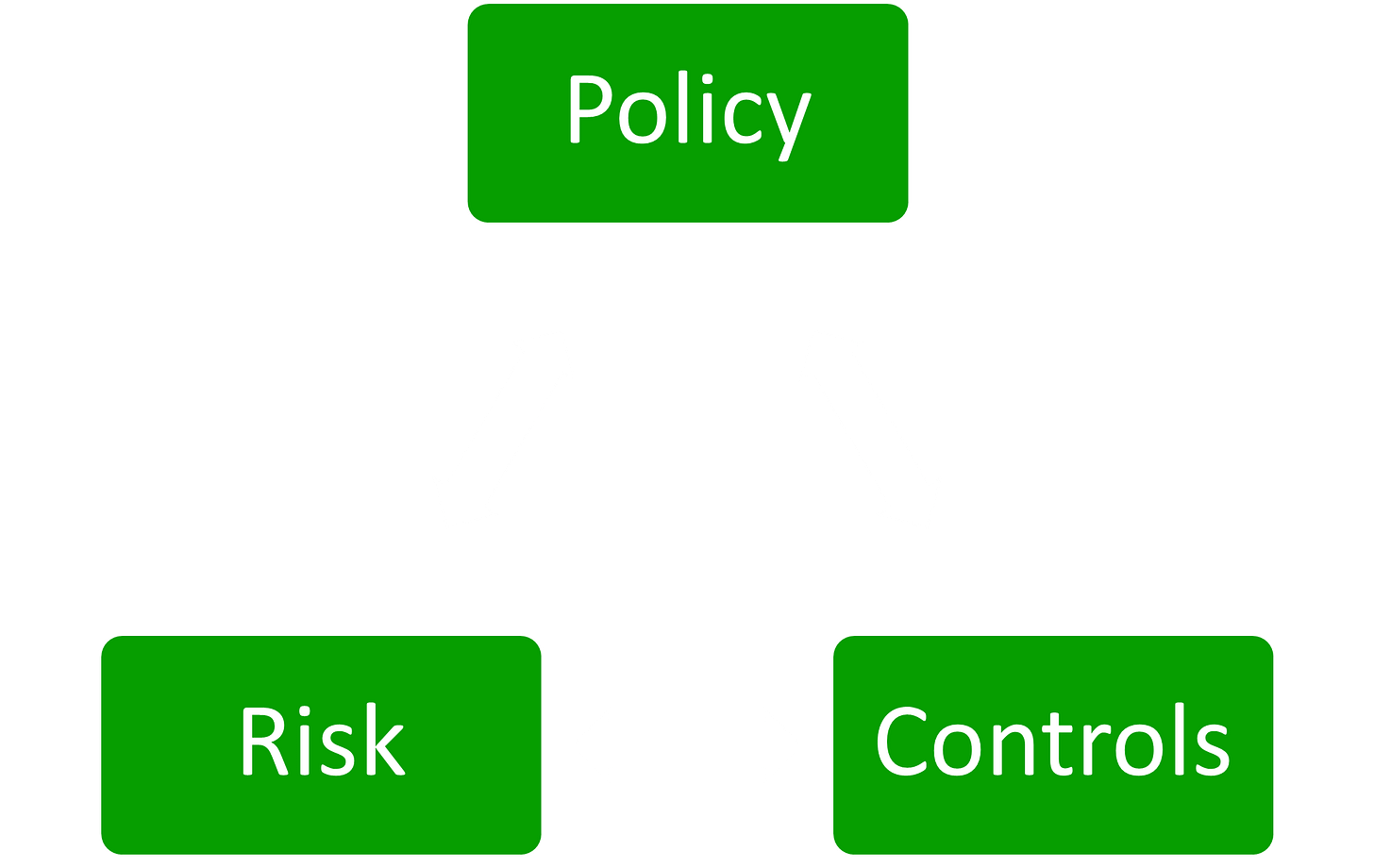
Policies are the root of all control.
We have our unwanted behaviours. These are our risks. If they happen, it will result in some form of harm to the organisation. So, we need to implement our security policies to tell our staff how we want them to behave. What is considered acceptable behaviour? What configurations to use? This is important, and we need to document it and ensure that our staff know what is expected of them and what will happen if they do not follow the rules.
There is a lot to consider. There is a lot for our staff to learn and do. We can make it easier for them by implementing controls that make the unwanted behaviour less frequent. Sometimes, the control can stop it altogether.
It’s a feedback loop. Changing the risks will require changes to the policies and the controls used to mitigate the risk. It’s all controlled by the policies.
Building for Compliance
Many companies will only focus their security policies on what is required by security frameworks like ISO 27001. That standard has a mandatory requirement for companies to have nine security policies before getting the certification. Compliance does not equal security. Building for compliance will make an organisation more secure, but all of the standards could be better. Then, we have the problem of reactive policies.
Somebody does something stupid, and the company makes a policy to try and stop it from happening again. That just doesn’t work. You end up covered in policies designed to fix problems, not prevent them from happening in the first place. If we build for security, we can avoid this problem and become mature organisations with policies designed to deal with security first. This results in having the proper defences and controls in place to stop the cuts from happening in the first place.
We want to build for security. We know that we have risks and need policies to control them. How do we do it? What risks do we need to manage? What policies do we need to write?
Risk Scenarios
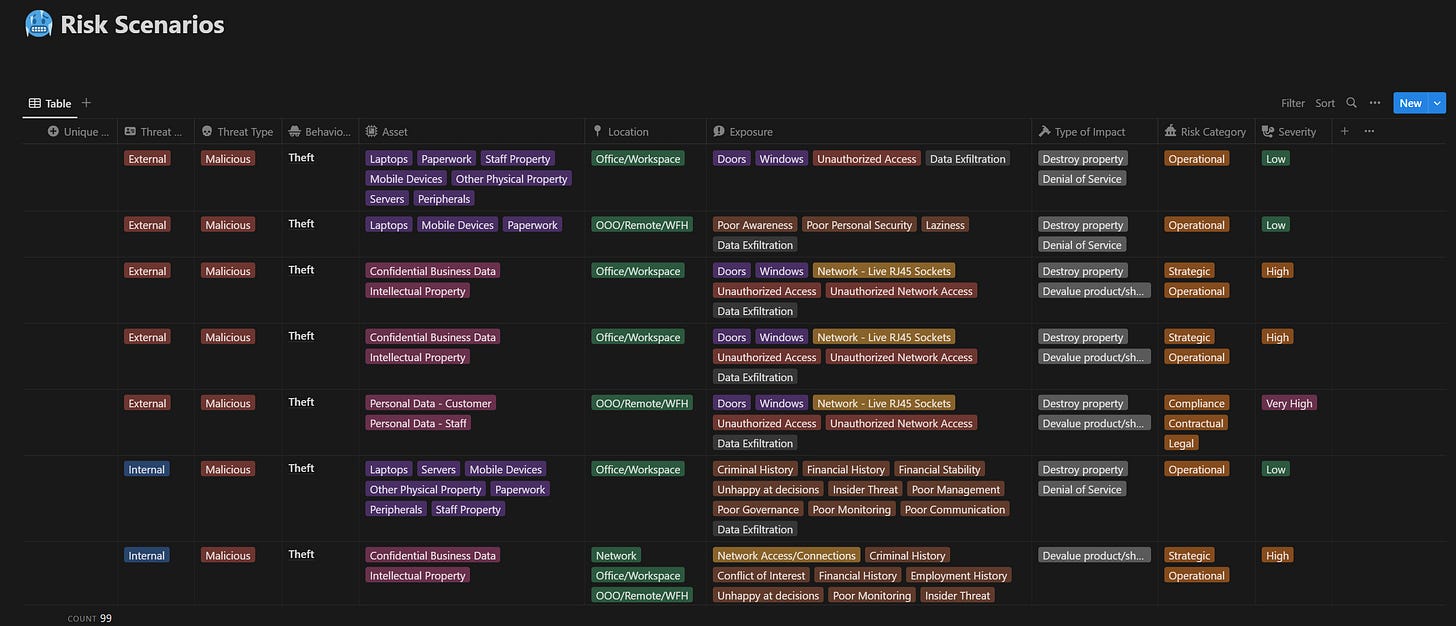
Before controlling potentially harmful behaviour, we must understand what behaviour we might be exposed to. We need to carry out an assessment of the risks that could harm us. We do that by looking at our environment and seeing where we are vulnerable. I don’t mean vulnerability management. If someone walked into the building and stole the finance server, what harm would that cause? How do we stop it? That’s a risk scenario.
This is a proprietary database of 98 risk scenarios that I have created. It looks at generic threats. I select if the behaviours can be caused by someone internal or external, malicious or accidental. Then, I look at the assets it could affect, the location of the asset, and the areas of weakness for the potential vulnerability. I then need to ensure a policy that targets and mitigates the risk. We do that by carrying out a Gap Analysis against the Policy framework.
Security Policy Framework
The policy framework is the database or repository we use to track security policies and procedures.
If we have a risk scenario not covered by a policy, we need to amend an existing policy or draft a new one that does. This is my policy repository. It’s a Policy Management Solution provided by Xoralia. Their brilliant policy management solution allows companies to control policies, manage the policy lifecycle, and track the reader’s attestation. The best thing about it is that it integrates with SharePoint. So, companies don’t need to move their policies outside the network.
Control Register
You need a control register after completing the risk scenarios and your policy framework. A method of tracking all the controls that the organisation has in place to reduce unwanted behaviour.
Summary
In summary, we learned that security is about feelings of comfort and safety. We learned that people feel insecure because of natural disasters, potentially dangerous animals, and the unwanted behaviour of others. We learned that the purpose of the security function is to advise businesses on managing operating conditions to enable them to generate revenue in places where the risk of unwanted behaviour is minimal. We learned about the two types of security control and their sub-types. I wrote about how security policies are the root of all control. It’s how we control the mitigation of all security risks. We learned about Risk scenarios and how they can be used to target risks. Then we looked at a Policy framework, and I wrote about a control register.
How can I help?
This methodology is how I create a strategy for implementing a security policy framework and help clients meet the requirements of laws and security standards like Cyber Essentials, GDPR, and ISO 27001. If you’d like to talk to me about working with you to implement a security standard at your small or medium-sized business, you can send me a DM on LinkedIn or book a Strategy Call on my services page, where you will find more information.
That’s it for this week. I hope you’ve enjoyed learning about the objective of a security function and how I help my clients achieve it. Let me know what you think in the comments or on LinkedIn. If you liked it, consider sharing it with your peers.
Until the next adventure!
Stuart Wedge 🧙♂️
PolicyWizard