🧙♂️ Security Policies for Small Business
The Fellowship - Week 10
Welcome to the tenth edition of The Fellowship Newsletter.
Last week I wrote about Choosing a Standard and the four key drivers for security policies. In the section > Legal or Regulatory Obligations, I made a mistake. I wrote:
“GDPR obligated countries within the EU to enact a law specific to their jurisdiction that enforces the regulation. In the UK, that law is the Data Protection Act (2018), revised in 2022.”
That is a misunderstanding of the regulation on my part. The correct statement should have read:
“GDPR is enforceable within all areas of the European Union as a stand-alone regulation. It allows member countries of the EU to add requirements. In the UK, the Data Protection Act adds to GDPR and is not the UK’s implementation of GDPR.”
Thank you to Dr Mike Brass for pointing out the mistake.
This week I respond to a question from Ben Brown of Ronin PenTest, who asked:
As a small but growing business, what are the most important policy areas to pay attention to, and where are the biggest/quickest wins to be found?
Thank you for this question, Ben. As I work in an Enterprise level company, it’s easy to overlook how security policies and procedures can be used effectively in smaller organisations. I’m happy to dig into this area to help people like you who may have a few staff and want to know where to focus.
The first question you need to ask is, “Why?”. This ties into last week's newsletter. What is your reasoning for wanting security policies and procedures? What is driving you to need them? Are you doing it because there’s a regulation or law you need to comply with? Has a customer asked you for a certification like ISO 27001? Do you want to give your staff clear instructions? It might help reduce the number of questions you need to answer. Or are you trying to improve security because you know that good security is good business practice? Protecting your ability to create value will help keep the money coming in. You’re making it harder for somebody to come and take the value you have created with your product or service.
Once you know your drivers, you can start to build a plan. I covered it in a fair amount of depth last week in section 4: Continuity of value generation. As a recap, you will need to:
Assess the environment:
What do we have?
What can we not afford to lose?
What do we not want to be harmed?
What, if harmed, can we repair quickly?
Assess the types of behaviour that could cause harm.
Assess what controls you have in place to stop harmful behaviour.
Assess what controls are deficient and should be implemented to stop harmful behaviour.
Once you know what controls you need, you will need to implement them in Security Policies and Procedures. This is how you communicate the “management requirements” for security practices.
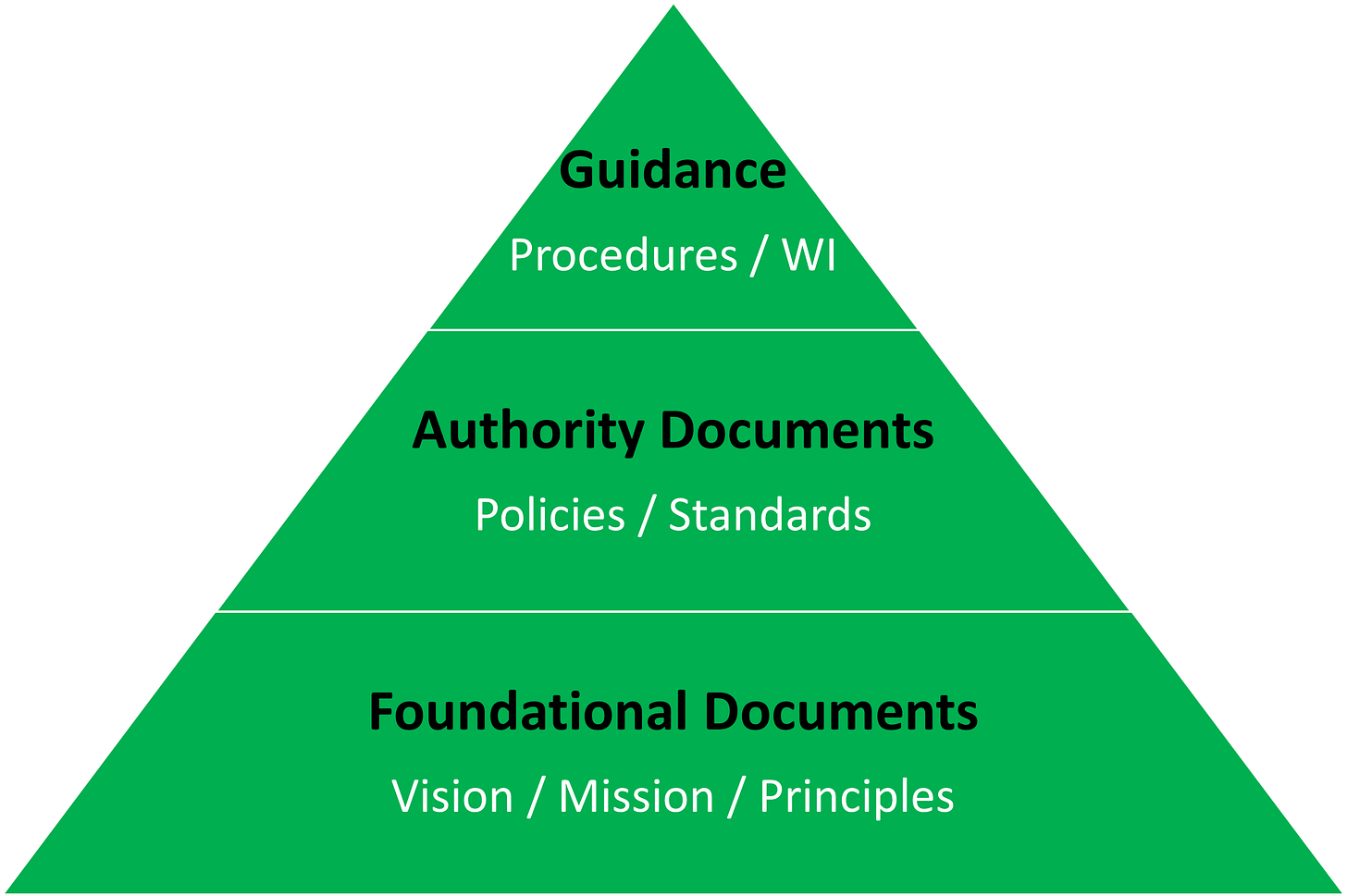
What are Authority Documents?
In business, we have three different levels for document status. First, we have our foundational documents. This can include the board’s vision for the company, mission statements, and principles that the business uses to manage its business effectively.
Second, we have our authority documents. These are the policy instruments. Fact-based statements instruct staff on the management requirements for different business areas.
Lastly, we have our guidance. This is our standard operating procedures, work instructions, and any educational or background information that we use to communicate the policy requirements.
In my course, I describe five different types of policy documentation. Those five types all fall within the top two layers of the Authority Document pyramid. This graphic shows how using the business vision, mission, and principles set out the foundations for our documentation, then building on the sturdy base with the policies, and then the guidance is how we finish it. The three-tier process set our stall on how to manage the security framework of our business.
Without knowing your business, drivers, vision, mission, principles, environment, or controls, I’m not going to sit here and pontificate over what you should do. Instead, I will tell you how I would do it if I grew a small business.
How would I implement a Security Policy Framework in my small business?
The big things to think about are privacy and security. Working in the UK, I am subject to the UK GDPR. As such, I must tell my customers (and those who use my free resources like this newsletter) what I do with their data. If you are collecting the data of your customers, you need to do the same.
There are a whole bunch of things that you need to do around personal information. This is not a lesson for that. One of the things that you’ll need to do is write a Privacy notice.
Draft a Privacy Notice
A privacy notice is a publicly available document where you describe your business's different touch points with the personal information of your customers and potential customers. You’ll need to be open with them, providing the reasoning for collecting the information.
Give them contact details for someone in the business who can answer questions on the use of their data. They should also know their rights and who to contact to make a complaint.
The next thing I would do is write an Information Security Policy.
Draft an Information Security Policy (ISP)
This document can be written for any one of the four policy drivers. It can show due diligence regarding a legal requirement, it can be requested as part of a security framework like ISO 27001, and it can be used to communicate the requirements of operational security configurations to ensure consistency across the business.
There are a lot of conflicting views about what should be included in an Information Security Policy. Some companies treat this document as a catch-all for everything related to security. My first contract job was for a financial services company in the United States of America. They sent over their ISP, which was over 40 pages long and full of utter incomprehensible waffle and legal rubbish. You’ll remember that one, Ben. We worked on that contract together.
They had used it as a dumping ground. There was procedural stuff for unrelated business processes, names of different people, and detailing tasks they had to do. It was bad. We fixed it for them, and working on that contract helped me learn what a bad Information Security Policy looked like.
ISO 27001 Policy Requirements
If you’re implementing ISO 27001, you need to meet the requirements of section > 5.2 Policy. In my words, the requirements are that the policy:
Should be suitable for the business type and purpose.
Should include the objectives for Information Security or provide a framework.
Should include a management commitment to meet the objectives.
Should include the management's commitment to continually improving the Information Security Management System (ISMS).
Should be documented (published, not verbal).
Should be communicated to everyone in the business.
Should be available to other interested people who may need to know how the business manages information security. Those people might be law enforcement, regulatory bodies, or customers. Some businesses publish their ISP on their websites.
Consider keeping the ISP short. Include only what you need for the standard, and then include some clear and concise policy statements for the specific ISMS functions detailed within the ISO standard. Just because the standard requires nine mandatory policies doesn’t mean that you need to have nine documents.
What Policies are mandatory for ISO 27001?
Here are the nine mandatory policies within ISO 27001:
(5.2) Information Security Policy
(A6.2.1) Mobile Device Policy
Include BYOD
(A6.2.2) Teleworking Policy
(A9.1.1) Access Control Policy
(A10.1.1) Cryptographic Control Policy
(A10.1.2) Key Management Policy
Join this policy statement with the Cryptographic Control Policy.
(A11.2.9) Clear Desk & Screen Policy
(A12.3.1) Backup Policy
(A15.1.1) Supplier Relationships Policy
Quick Wins
To answer the last part of the question, if I wanted to have the quickest wins with security policy without worrying about ISO 27001, I’d implement only these:
Privacy Notice
Information Security Policy
Acceptable Use Policy Statement
Access Control Policy Statement
BYOD & Mobile Policy Statement
Encryption and Key Management Policy Statement
Network Security Policy Statement
Password Policy Statement
Privileged Account Policy Statement
Remote Working Policy Statement
Safe Handling of Information Policy Statement
Policy Enforcement Statement
Getting deeper into the weeds
Policy statements are very high level. Sometimes a high-level statement is not sufficient. Take the Password Policy Statement as an example. This is an area that can go quite deep. You may have many different environments with similar but slightly differing configuration requirements.
If you want to keep the ISP concise, we need to use other methods to introduce specific configuration requirements. We can do that by introducing a standard. A fact-based collection of controls or settings that we want our staff to use. Standards can be separate documents or included as an appendix to the ISP. Here are examples of both:
Statement
[Company] requires that all systems are configured to require a password and that the password be configured to meet the complexity and length requirements of the [Company] Password Standard.
[Company] Password Standard
The Password length is 24 characters or more.
The password contains at least one uppercase letter (e.g., A, B, C), at least one lowercase letter (e.g., a, b, c), at least one numerical character (e.g., 1, 2, 3), and at least one special character (e.g., “, £, $, %).
Policy Templates
Many businesses find implementing new security policies daunting, especially those trying to implement the ISO standards. If you look online, you’ll find many companies offering template policy packs with upwards of forty policies. You do not need all those documents. You only need the policies applicable to your business. If you buy a policy pack or download a policy from another organisation, customise them to communicate how you have implemented security controls for your business. If you don’t, you’re opening a can of worms that will lead to future problems and potentially legal or compliance issues. PolicyWizard only offers bespoke policies. We work with businesses to implement the right policies and procedures for them.
Conclusion
Implementing security policies is vital to building good security practices into the foundations of a growing business. Implementing them early shows your staff and customers that you care about protecting personal information. It takes far more time and money to implement security policies once the business matures to a level where you have hundreds or even thousands of staff. Additionally, customers are more likely to spend their money with a business that takes care of their information.
How can I help?
For small businesses, there are three options:
1. Book a free 15-minute policy strategy session.
2. Book a 90-minute consultation to talk your requirements over in depth.
3. Take the Security Policy Foundations course if you want to do it yourself.
For more information on my services, please visit my Services page.
That’s it for this week. I hope you’ve enjoyed learning about security policy implementation in a small but growing business. Let me know what you think in the comments or on LinkedIn. If you liked it, consider sharing it with your peers.
Until the next adventure!
Stuart Wedge 🧙♂️
PolicyWizard